External Attack Surface Management
We look at your surface the way attackers do—same logic, mindset, and timing.EASMWe verify what’s exploitable before we escalate—so you get a short, evidence-backed list, not thousands of raw alerts. Audit-ready proof and security assurance that stand up to regulators and insurers, plus zero-day detection 7 days ahead of CVEs.
Why External Assurance Has to Be Defensible
Unmonitored or unverified surfaces create blind spots and proof gaps. We deliver continuous, audit-ready evidence so you can show what you found, when, and what you did.
External Exposure Blind Spots
Unmonitored internet-facing assets create silent risk and unaccounted attack paths—attackers find them first.
Verification Gaps
Findings without external proof don’t hold up to regulators, insurers, or post-incident reviews.
Assurance Over Time
Compliance and security both need continuous evidence of monitoring and drift—not one-off scans.
Discovery is easy; validation is the bottleneck. Many tools dump raw scanner output—but in real environments a large share of findings aren’t exploitable in context (auth, WAF, dead assets). We verify first, then escalate: a short, evidence-backed list instead of noise.
Complete EASM + Regulator Assurance
Attacker-grade discovery and evidence-grade visibility for security teams, compliance, regulators, and insurers.
Attacker’s View: Logic, Mindset & Timing
We look at your applications and external surface the exact way attackers do—same discovery logic, prioritisation, and timing—so you see what they see, with proof.
Verification-First Findings
We only escalate what we can prove is exploitable—with proof artifacts and attack-path context. Less triage, faster remediation, stronger credibility with regulators and insurers.
Audit-Ready Reporting
Explainable, deterministic reports for security teams, regulators, and insurers.
Continuous Assurance
Daily refresh, drift detection, and zero-day monitoring to prove you stayed secure over time—with alerts 7 days ahead of CVE publication.
One View of Your External Attack Surface
The Attack Surface dashboard gives you a single, evidence-backed view of what’s exposed—and what changed—so you can act and prove it.
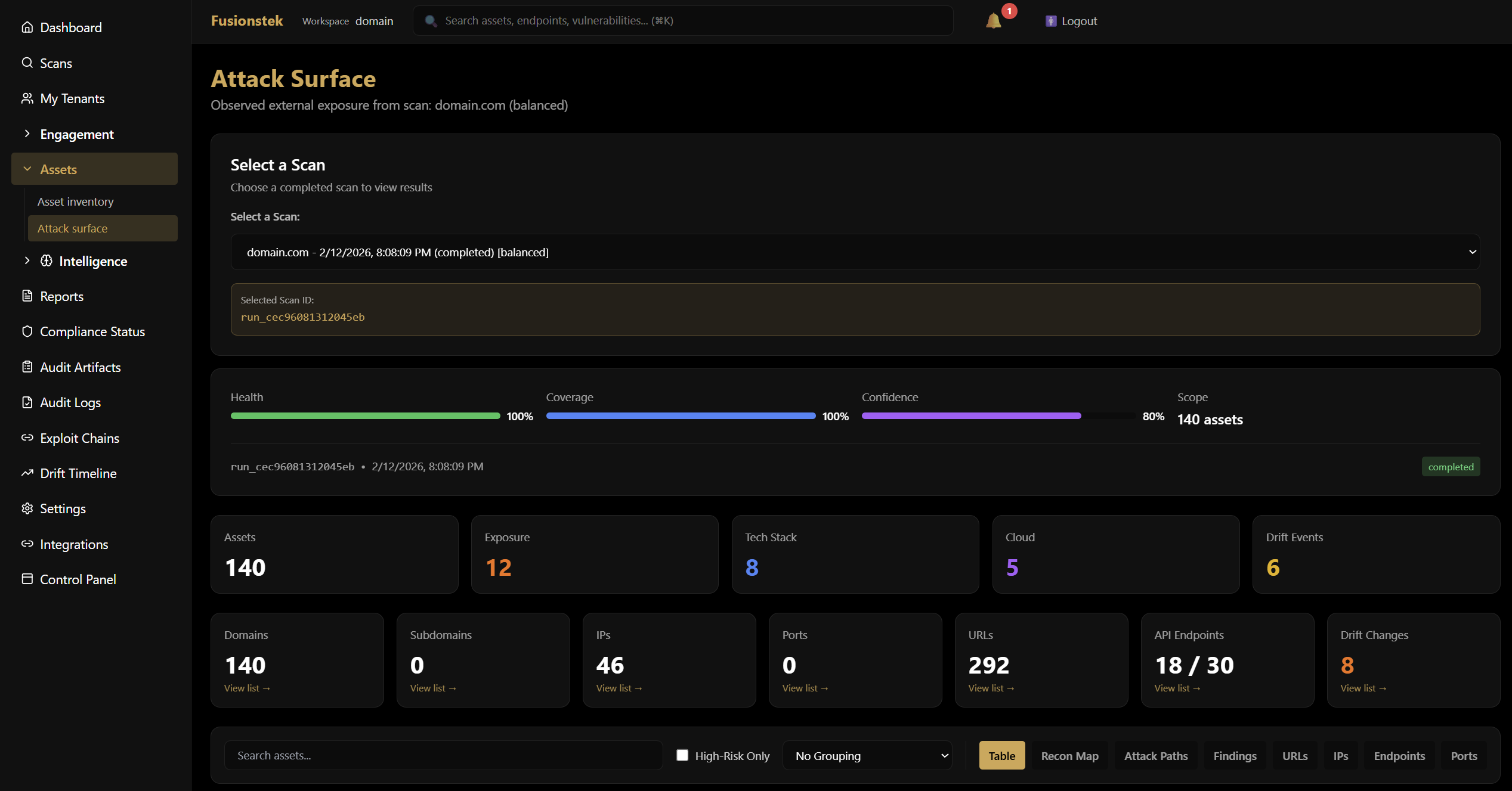
Choose a completed scan and see everything we found: domains, subdomains, IPs, open ports, URLs, and API endpoints in one place. Health, coverage, confidence, and scope scores show you how thorough the run was—and drift events show exactly what appeared, changed, or disappeared since the last run.
That’s the same view your security team uses to prioritise risk and the same evidence you can point to for regulators and insurers: attacker-grade discovery, with verification and timelines built in.
- Full asset inventory per scan
- Health, coverage, confidence, scope
- Drift detection and change tracking
- Audit-ready evidence in one dashboard
Zero-Day Detection: 7 Days Before CVEs
Detect threats 3–7 days before CVE publication. Asset-specific correlation, version-aware precision, zero infrastructure overhead—no agents required.
Pre-CVE Visibility
We monitor GitHub security releases and Exploit-DB so you’re alerted within 24–48 hours of disclosure—before CVE publication.
Asset-Specific Alerts
Only technologies we detect on your attack surface trigger alerts. No noise for software you don’t run.
Continuous, No Re-Scans
One baseline scan powers monitoring every 10 minutes. Zero agents, zero performance impact.
Intelligence: Leaked Credentials & Breach Visibility
We monitor known breach exposures for your domains and identities. Trusted, enterprise-grade breach data—no legal gray areas, no shady collection methods.
Domain-Level Breach Visibility
See which of your domains have exposed credentials, which breaches they came from, when the breach occurred, and the type of data exposed (emails, passwords, etc.)—all from a single, authoritative source.
Trust & Credibility
Widely trusted by enterprises—used by Microsoft, governments, and security vendors. No password values are ever exposed; data is sourced through transparent, legally clear methods you can stand behind in audits.
Dashboards That Make Sense
Leaked credentials by domain, top exposed domains, exposure timeline, and breach severity summary—so you can prioritize and report with confidence.
How It Works
Deterministic discovery, verification, and evidence—no guesswork.
Submit Scope
Provide domains and approved scope under your policy.
Discover & Map
We enumerate internet-facing assets and build a verified surface map.
Verify & Analyze
Findings are validated with evidence, not assumptions.
Deliver Evidence
Receive audit-ready reports and continuous assurance tracking.
Use Cases
External assurance for regulated, internet-facing organizations
Enterprise External Assurance
Defensible visibility across complex domain portfolios.
- Multi-domain scope control
- Audit-ready evidence
- Drift tracking over time
E-commerce & Public SaaS
Continuous proof that customer-facing surfaces stay secure.
- Verified reachability + findings
- Policy‑approved edge posture checks
- Daily refresh cadence
Regulated & High-Risk Industries
Assurance built to satisfy regulators and insurers.
- Due-care timeline
- Verification ledger
- Policy-enforced guardrails
Trusted by Security Teams
Assurance outcomes that security leaders expect
“We finally have external assurance we can defend—clear evidence, timelines, and verification.”
Security Leadership
Enterprise · CISO Office
“Attacker‑grade discovery plus audit‑ready reporting closed our compliance gaps fast.”
Risk & Compliance
Financial Services · Security Team
“Daily assurance with verified findings gave us confidence without risky testing.”
Security Operations
Public SaaS · Engineering
Ready for EASM That Thinks Like an Attacker?
See how we deliver external attack surface management—same logic, mindset, and timing as attackers—with audit-ready evidence for security and compliance.
Book a Demo